The manuscript related to this project is currently under peer review. A draft of the work is available here.
![]()
People fall victim to email phishing attacks all the time, being tricked into revealing sensitive information like passwords or credit cards numbers. But what is it about the email that allows it to trick the recipient? Are there certain tactics that are most effective? Are some people simply more susceptible?
We designed a study to attempt to answer these questions. To do this we coded a large corpus of emails -both phishing and legitimate- according to the persuasion principle or principles used within the email. Participants then performed a judgement task where they were asked to decide if they thought each email was legitimate or a phishing attempt. This let us document the effectiveness of various persuasion principles, as seen below.


You might notice that the order of persuasion principles almost perfectly flips between the legitimate and phishing emails. For instance, phishing emails that use the Authority/Scarcity (A/S) combination are most likely to be correctly labeled as a phishing attempts. But when legitimate emails use the A/S persuasion principle, they are most likely to be incorrectly labeled as a phishing attempt. What this suggested to us is that persuasion principles invoke heavy bias- some persuasion principles result in emails always assumed to be safe, other result in emails always assumed to be phishing attempts- regardless of whether the email actually was a phishing attempt or not.
This pattern of findings suggested a Signal Detection Theory approach would be of value. Signal Detection theory classifies responses as hits, misses, false alarms, or correct rejections. It also provides a measure of sensitivity (how well the signal can be differentiated from the noise), and reveals the decision criterion- the bias that each persuasion principle invokes. Signal Detection Theory graphs for 2 of the persuasion principles can be seen below.
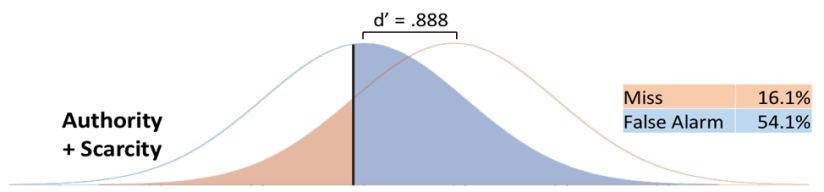
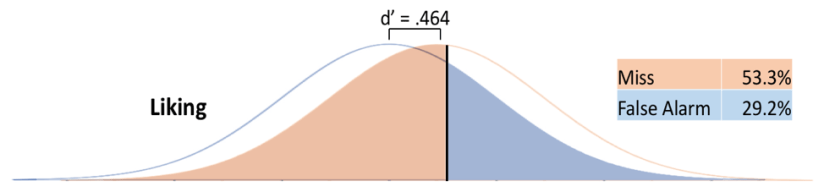
In addition to these Signal Detection results, we conducted linear regressions to assess the factors contributing to email phishing susceptibility. These models included not only the persuasion principles used in each email, but the personality and demographic profile of the recipient, as well as any potential interactions between the two.
We hope to use these data to describe a more comprehensive model of email phishing susceptibility.
